Testing Nessus in the Lab
Nessus in a Nutshell
Nessus is a enterprise grade vulnerability scanning tool with a free/community version called Nessus Essentials, usable for 1 year. They do, however, have a large paid version with some minor differences including an installable agent for quicker deployments to large groups and faster scans. This Essentials edition only allows for the scanning of 16 total assets. I built my Nessus VM on Debain with the GNOME GUI, powered by 2 cores and 4GB of ram. While this is below the recommended specs, it scanned my 4 IPs perfectly fine. It should be noted, the GUI was removed after configuration to conserve RAM usage.
Setting up the Scans
The setup for Nessus was quite easy, as was the setting up of scans. It allows for the scanning of IP ranges, but I input specific IPs for my VMs, Host, and another devices to test it out. My Windows machine is behind an update and I wanted to see if it would catch this in its “Deep Scan” after playing around with some non-credentialed scans. To do this, I set up a new account on each device to act as a service account. Being as I only had 4-5 devices, doing this manually was not an issue. Once the accounts were set up, I configured my scan.
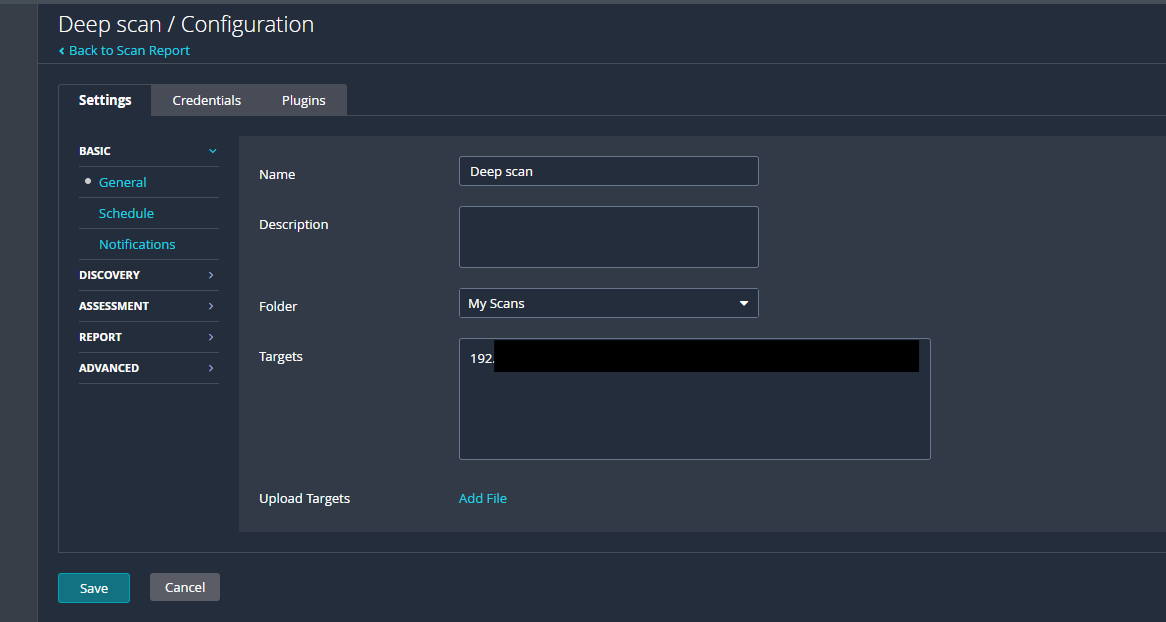
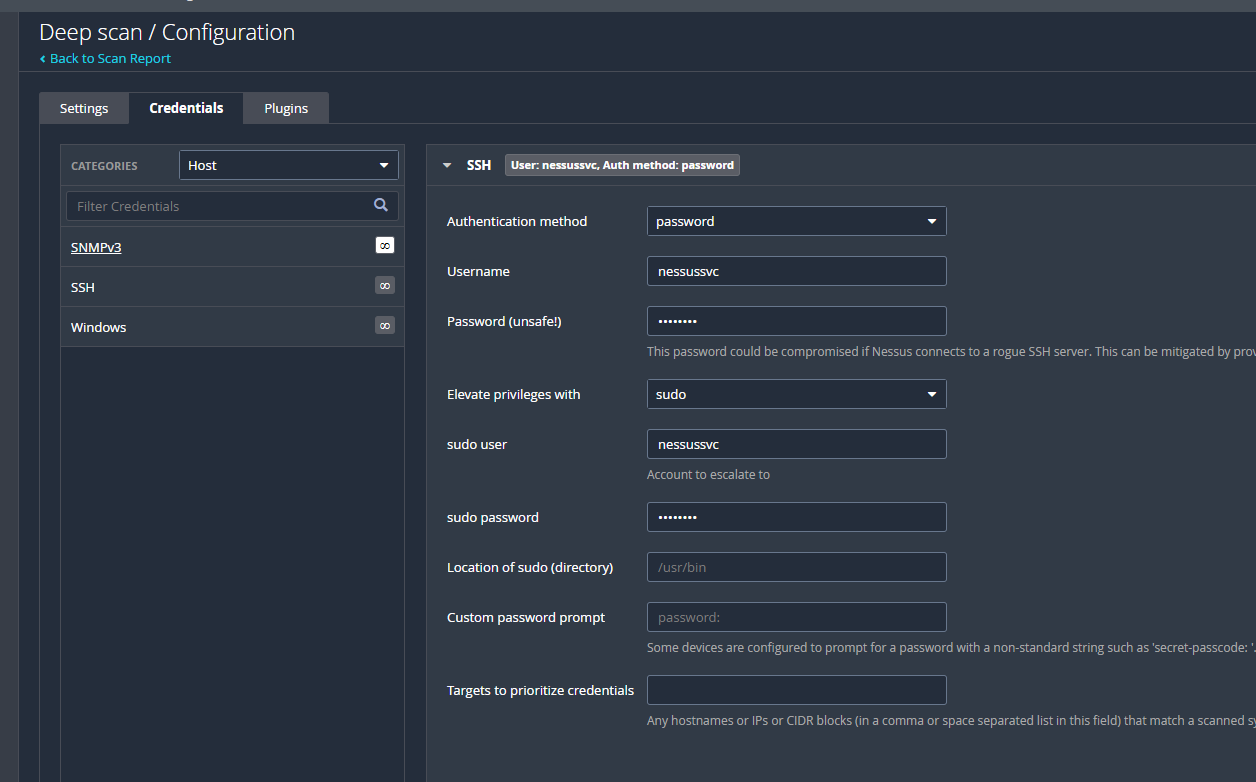
This is the basic look of the configuration I used, it was all defaults for “Deep Scan”.
The Results
The scans took a few minutes as they were credentialed but were very in depth! I was surprising in both a good way and a bad way. I will explain that further down.
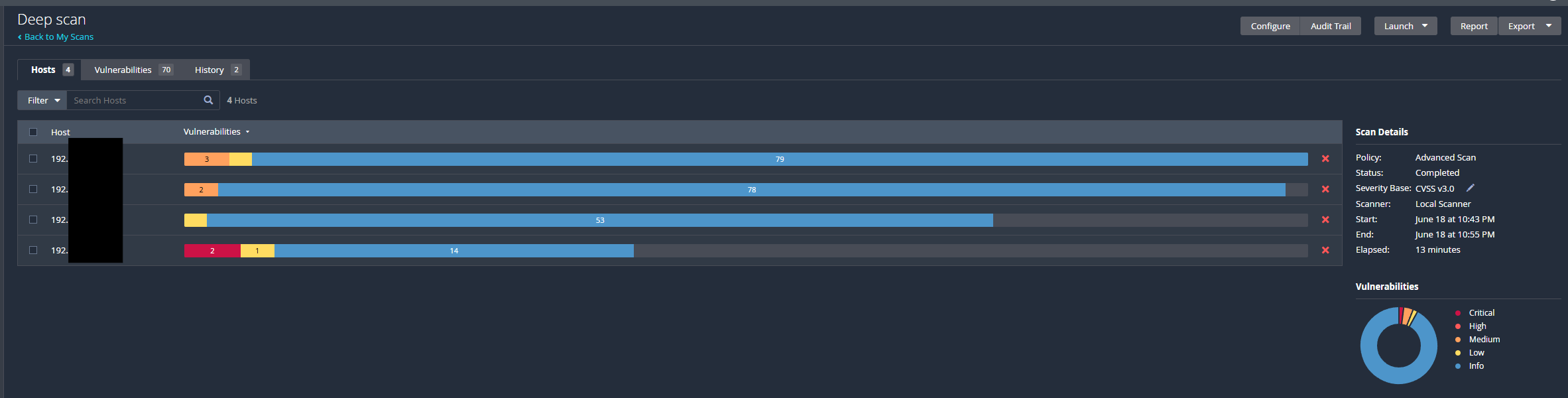
The Minecraft server that was built for my previous post required port forwarding which was one of the vulnerabilities picked up with the scan.

The most surprising part of all, was that Nessus proceeded in one of it’s vulnerabilities it detected, to screenshot the screen of the device it was able to access! While the screenshot was not of anything, the fact Nessus attempted to do so as a way of proving the attack was impressive.
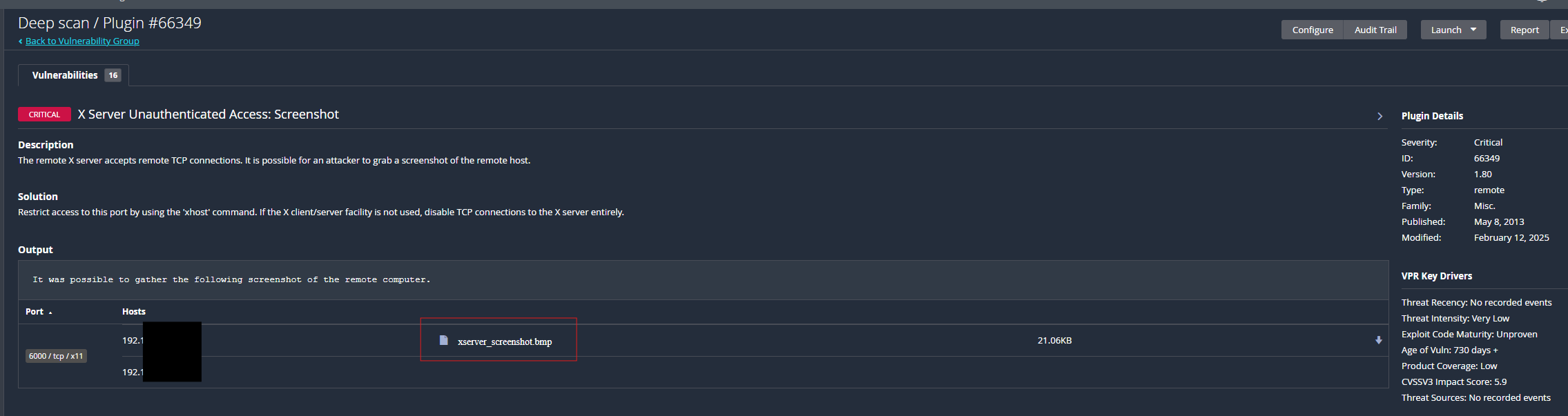
The part of this that was a bit surprising in a negative manner is that Nessus was unable to detect any Windows/Microsoft CVEs on the machine. I assume that this is likely due to it being in the Insider Preview update channel. Nonetheless, for a pure scanning software Nessus is very competent. I plan on testing others including Wazuh in order to determine what I want as a permanent fixture in my home lab environment.